What is Microsoft Entra ID?
Microsoft Entra ID, previously known as Azure Active Directory, is a service based in the cloud that manages identity and access. It allows your workforce to use external resources like Microsoft 365, the Azure portal, and many other SaaS applications. Additionally, it facilitates access to internal resources such as intranet apps and any cloud apps developed by your organization.

The benefits of Microsoft Entra ID vary depending on the role within your organization:
- IT administrators utilize Microsoft Entra ID to regulate access to applications and their resources, based on the needs of the business. For instance, they can enforce multi-factor authentication for accessing crucial organizational resources.
- Application developers can leverage Microsoft Entra ID as an authentication provider that adheres to standards. This helps them incorporate single sign-on (SSO) into applications, which works with a user’s pre-existing credentials.
- Subscribers of Microsoft 365, Office 365, Azure, or Dynamics CRM Online are already utilizing Microsoft Entra ID, as every tenant of Microsoft 365, Office 365, Azure, and Dynamics CRM Online is automatically a tenant of Microsoft Entra.
Microsoft Entra ID is acknowledged as a leader in the field of managing directories, enabling application access, and safeguarding identities. It amalgamates core directory services, application access management, and identity protection into a singular solution.
What Exactly is Changing in Microsoft Entra ID?
Microsoft Entra ID, formerly known as Azure Active Directory, is undergoing a series of enhancements to improve its functionality and user experience. These are:
New Microsoft Entra Home Page: The homepage of the Microsoft Entra admin center has been redesigned. This is to help users understand the product better, identify ways to make the most of its features, and stay updated with recent announcements and new features.
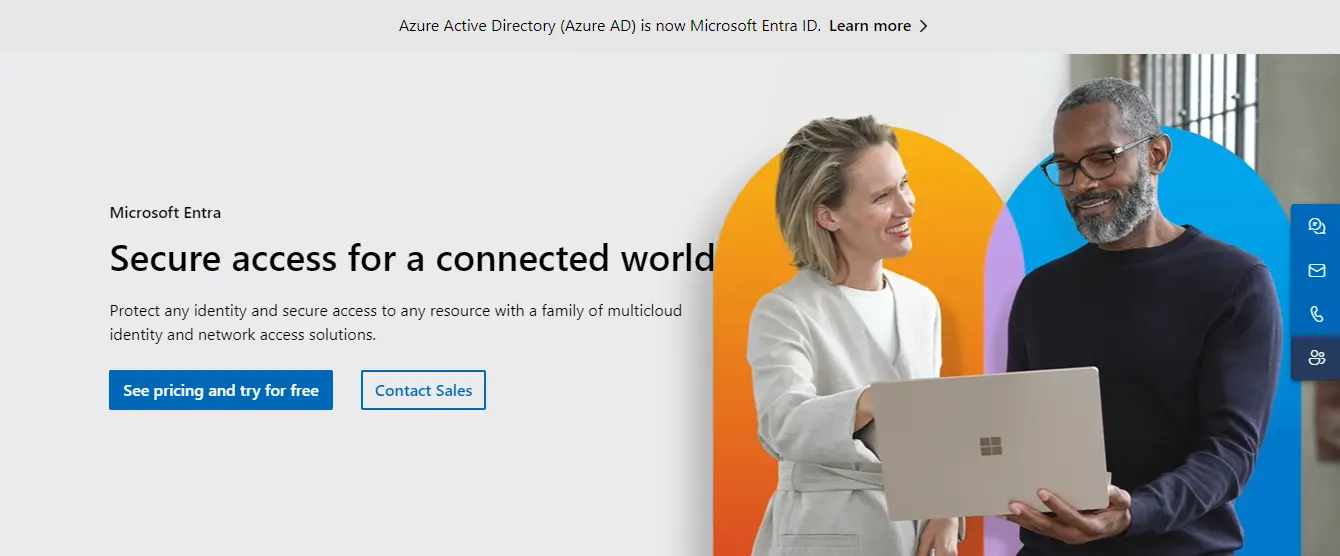
Cross-Tenant Manager Synchronization: This is a new feature that allows the synchronization of the manager attribute across different tenants. A tenant in this context refers to a dedicated instance of Microsoft Entra that an organization receives when it signs up for a Microsoft cloud service like Microsoft 365.
Microsoft Defender for Office Alerts in Identity Protection: This feature integrates alerts from Microsoft Defender for Office into Identity Protection. One such alert is the ‘Suspicious sending patterns’ risk detection. This alert is triggered when someone in your organization sends an email that is deemed suspicious.
New Microsoft Entra Recommendation to Migrate off MFA Server: Microsoft Entra is recommending customers move from MFA Server to Microsoft Entra multifactor authentication. This is because the MFA Server will be retired on September 30, 2024.
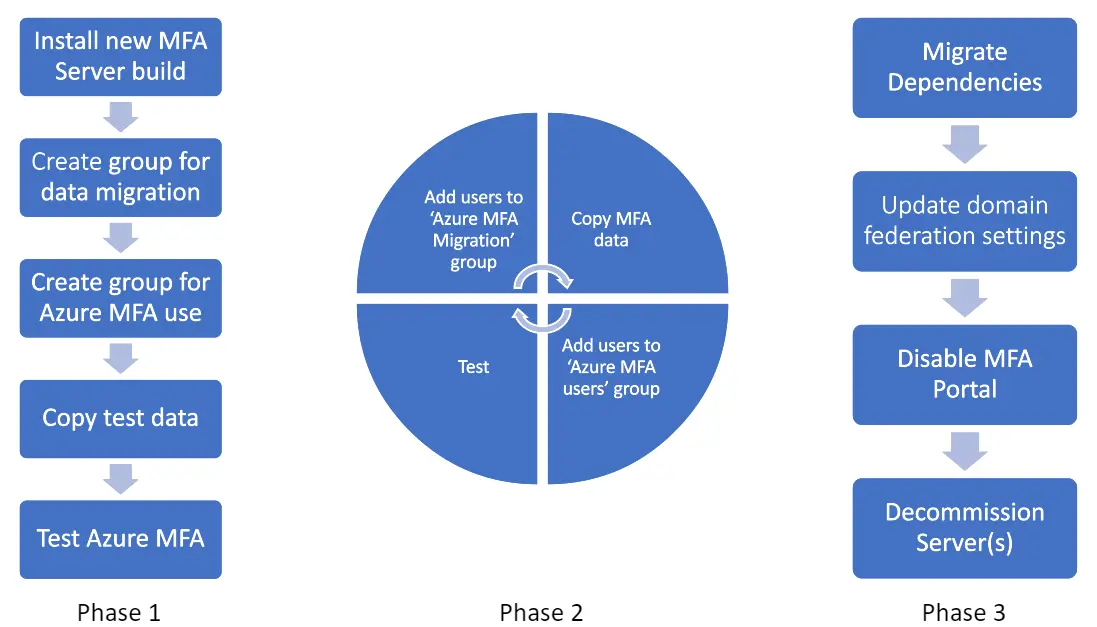
Microsoft Security Email Update and Resources for Azure AD Renamed to Microsoft Entra ID: Azure Active Directory (Azure AD) has been renamed to Microsoft Entra ID. This is just a name change and all existing deployments, configurations, and integrations will continue to function as they do today without any action from you.
Difference Between Microsoft Entra ID and Windows AD
Here is a quick comparison between Azure AD and Windows AD:
| Microsoft Entra ID | Windows Active Directory | |
| Communication | Representational State Transfer (REST) APIs | Lightweight Directory Access Protocol (LDAP) |
| Authentication | Cloud-based protocols like OAuth2, SAML and WS-Security | Kerberos and NTLM |
| Network Organization | Tenant – Flat structure of users and groups | Organized into Organizational Units, Domains and Forests |
| Entitlement Management | Admins organize users into groups and enable groups to access apps and resources | Admins or data owners assign users to groups |
| Devices | Mobile device management | Does not manage mobile devices |
| Desktops | Windows desktops can join Microsoft Entra ID | Desktops are joined to Windows AD and governed by Group Policy (GPOs) |
| Servers | Uses Domain Services to manage servers | Managed by GPOs or other on-premise server management system |
Features
App Integrations and Single Sign-On (SSO): This feature allows users to access all their applications from any location or device with just one set of credentials. This simplifies the process of accessing applications.
Passwordless and Multifactor Authentication (MFA): These are strong authentication methods that enhance security. Passwordless authentication eliminates the need for passwords, while MFA requires multiple methods of verification.
Conditional Access: This feature allows organizations to set policies that control access to resources based on certain conditions, enhancing security without compromising user experience.
Identify Protection: Microsoft Entra ID provides tools to protect user identities and credentials automatically.
Privileged Identity Management: This feature allows the organization to manage and control access to resources based on business requirements.
End-User Self-Service: This feature allows end-users to manage their own access, reducing the workload on IT admins.
Unified Admin Center: This is a central location where all identities and access to all applications can be managed.
Benefits
Secure Adaptive Access: Microsoft Entra ID provides strong authentication and risk-based adaptive access policies to protect access to resources and data without compromising user experience.
Seamless User Experience: It provides a fast, easy sign-in experience across your multi-cloud environment. It reduces time managing passwords and increases productivity.
Unified Identity Management: It allows you to manage all your identities and access all your applications in a central location, improving visibility and control.
Enhanced Security: It streamlines user authentication and enhances security.
Boost productivity: It boosts collaboration from any platform and device.
Use Cases
Account Onboarding: This reduces the time, cost, and risk associated with onboarding new employees.
Account Recovery: It enables an end user to recover or unlock their account using a self-service mechanism.
Secure Access to Resources: It provides secure access to both internal and external resources.
Integration with Non-Microsoft Services: It can be used as a unified identity provider to sign into your non-Microsoft services, like Google, AWS, Salesforce, and ServiceNow.
Management of Service Licensing: It is used to manage service licensing for Microsoft 365, Office 365, Enterprise Mobility + Security, and Microsoft Purview.
Microsoft Entra ID is used by more than 300,000 organizations and is consistently recognized as a Leader by industry analysts. It is a powerful tool for managing and securing access to resources in an organization.
Integration and Applications
Microsoft Entra ID can be integrated with many applications. This includes well-known applications such as SAP and those using standards such as OpenID Connect, SAML, SCIM, SQL, LDAP, SOAP, and REST. There are also tutorials available to guide you through the process of integrating common tools with Microsoft Entra single sign-on.
Pricing
Microsoft Entra ID comes in different editions with varying prices:
- Free: Included with Microsoft cloud subscriptions such as Microsoft Azure, Microsoft 365, and others.
- P1: Starts from $6.00 per user/month.
- P2: Starts from $9.00 per user/month.
Governance: Starts from $7.00 per user/month.
Security
Microsoft Entra ID provides robust security features:
- Authentication and Authorization: It supports multiple authentication methods, including biometric sign-in options with Windows Hello for Business, FIDO2 security keys, mobile phones with the Authenticator app, and more.
- Conditional Access: It extends Conditional Access policies with network conditions to protect against malicious internet traffic and other threats from the open internet.
- Identity Protection: Microsoft Entra ID Protection helps stop attacks before they happen by blocking identity takeovers in real time and automating attack mitigation.
Signing Up for Microsoft Entra ID
Create a Free Account: You can create a free account in one of two ways:
- Join the free Microsoft 365 Developer Program. This gives you access to a free sandbox, tools, and other resources, including a Microsoft Entra account with P2 licenses, configured users, groups, and mailboxes.
- Create a new tenant and activate a free trial of Microsoft Entra ID P1 or P2 in your new tenant.
Sign Up for Premium Editions: If you want to sign up for Microsoft Entra ID P1 or P2, you can do so through your Microsoft Volume Licensing plan. The program you choose depends on the number of licenses you want to get:
- For 250 or more licenses, you can use the Microsoft Enterprise Agreement.
- For 5 to 250 licenses, you can use the Open Volume License program.
Remember, it’s recommended to use your work or school account if you already have access to Microsoft Entra ID. However, you should use whichever type of account is associated with your Azure subscription.
For more detailed instructions, you can refer to the Microsoft Entra ID setup guide. It will help you configure the most important settings for Microsoft Entra ID and point you to additional resources for more complex environments.
In simpler terms, to sign up for Microsoft Entra ID, you first create a free account either by joining the Microsoft 365 Developer Program or by creating a new tenant and activating a free trial. If you want more features, you can sign up for a premium edition through your Microsoft Volume Licensing plan. The number of licenses you need will determine which program you should choose. It’s best to use your work or school account if you have one, but you can use any account associated with your Azure subscription. For more help, you can refer to the Microsoft Entra ID setup guide.
How do I Set Up Microsoft Entra ID for Your Organization?
Setting up Microsoft Entra ID for your organization involves the following steps:
- Create a Microsoft 365 Tenant: If your organization doesn’t already have a Microsoft 365 tenant, you will need to create one. A tenant represents an organization in Microsoft 365 and encompasses all the organization’s subscriptions, users, and groups.
- Sign In to the Microsoft Entra Admin Center: You need to use a Microsoft account to sign in, and you should have at least Global Administrator privileges. This ensures you have the necessary permissions to manage your organization’s resources.
- Configure Your Identity Settings: This step involves setting up the appropriate access levels for your administrators. This is crucial for managing your users and resources effectively.
- Add Users, Create Groups, and Assign Licenses: Before students and teachers can sign in and access the different Microsoft 365 services, they need a user account. There are several ways to add users, including using School Data Sync (SDS), synchronizing an on-premises Active Directory, or adding them manually. You can also use a combination of these methods.
- Configure School Branding (Optional): This step can help personalize the experience for your users. It might involve adding your organization’s logo, customizing the sign-in page, etc.
- Enable Bulk Enrollment (Optional): If you have a large number of users to add, this step can be helpful. It allows you to add multiple users at once, saving time and effort.
Remember, setting up Microsoft Entra ID is a fundamental step in managing user access and permissions for your organization. It helps ensure that only authorized individuals have access to your organization’s resources.
How do I Manage User Access and Permission with Microsoft Entra ID?
Default User Permissions: In Microsoft Entra ID, every user is given a set of default permissions. These permissions are determined by the user’s type, their role assignments, and their ownership of individual objects. You can only change these default permissions in the user settings in Microsoft Entra ID.
User and Group Permissions: Member users can register applications, manage their own profile photo and mobile phone number, change their own password, and invite B2B guests. On the other hand, guest users have limited directory permissions.
Manage Access to Apps: Microsoft Entra ID provides comprehensive access management for configured applications. This allows organizations to implement the right access policies, ranging from automatic, attribute-based assignment (ABAC or RBAC scenarios), through delegation, and including administrator management.
Assigning Users and Groups to an App: When assigning users and groups to a Microsoft Entra application, there are two primary modes of assignment: Individual assignment and Group-based assignment.
Manage User Profile Information: In the User settings area, you can modify several settings that affect all users.
Add and Manage Admin Accounts: If you want to grant administrative permissions to a user, you can add them to a Microsoft Entra role.
Each of these steps plays a crucial role in managing user access and permissions effectively in Microsoft Entra ID. It is important to understand each step to ensure the right access is given to the right users.
How do I Manage Access to My Custom App with Microsoft Entra ID?
Managing access to your custom app with Microsoft Entra ID involves several steps:
Register Your App: Sign in to the Microsoft Entra admin center as at least an Application Developer. Browse to Identity > Applications > App registrations. Select the app registration to which you are granting access to manage.
Create a Custom Application: Log in to the Azure portal and click Manage Microsoft Entra ID. Navigate to Enterprise Applications > All applications. Click +New application and then click Create your own application.
Configure Application Settings: In the Microsoft Entra admin center, in App registrations, select your application. Under Manage, select Authentication. Under Platform Configurations, select Add a Platform.
Manage Access to Apps: Microsoft Entra ID supports extensive access management for configured applications, enabling organizations to easily achieve the right access policies ranging from automatic, attribute-based assignment (ABAC or RBAC scenarios) through delegation and including administrator management.
Assigning Users and Groups to an App: Microsoft Entra application assignment focuses on two primary assignment modes: Individual assignment and Group-based assignment.